Hi
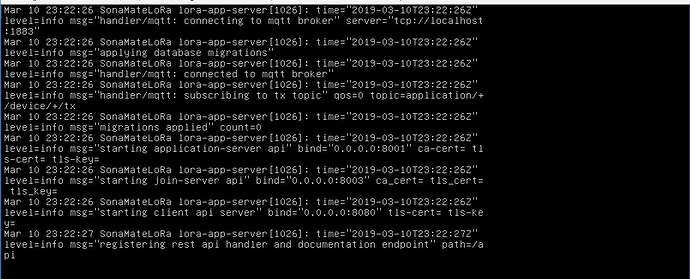
I am using DigitalOcean droplet with Ubuntu 18.04.2 x64. Installed LoraServer and LoraAppServer following the guidelines. In the LoaAppServer log output using
sudo journalctl -f -n 100 -u lora-app-server
shows msg=starting application server api bind=0.0.0.0:8001
it seems the current version of the lora-app-server.toml allows web-access.
can anyone please help …
Thanks
Silas
What does the output of journalctl show when you try to connect to the web interface at :8080
Check listening port of lora-app-server:
netstat -ltupn | grep lora-app
And don’t forget configure firewall:
Hi
I have attached two images here
And there is yet no firewall configured for Droplet on Digital Ocean
show yours lora-app-server.toml config
Hi, below is toml file content, it is the default, nothing changed but just for the credentials
[general]
# Log level
#
# debug=5, info=4, warning=3, error=2, fatal=1, panic=0
log_level=4
# The number of times passwords must be hashed. A higher number is safer as
# an attack takes more time to perform.
password_hash_iterations=100000
# PostgreSQL settings.
#
# Please note that PostgreSQL 9.5+ is required.
[postgresql]
# PostgreSQL dsn (e.g.: postgres://user:password@hostname/database?sslmode=disable).
#
# Besides using an URL (e.g. 'postgres://user:password@hostname/database?sslmode=disable')
# it is also possible to use the following format:
# 'user=loraserver dbname=loraserver sslmode=disable'.
#
# The following connection parameters are supported:
#
# * dbname - The name of the database to connect to
# * user - The user to sign in as
# * password - The user's password
# * host - The host to connect to. Values that start with / are for unix domain sockets. (default is localhost)
# * port - The port to bind to. (default is 5432)
# * sslmode - Whether or not to use SSL (default is require, this is not the default for libpq)
# * fallback_application_name - An application_name to fall back to if one isn't provided.
# * connect_timeout - Maximum wait for connection, in seconds. Zero or not specified means wait indefinitely.
# * sslcert - Cert file location. The file must contain PEM encoded data.
# * sslkey - Key file location. The file must contain PEM encoded data.
# * sslrootcert - The location of the root certificate file. The file must contain PEM encoded data.
#
# Valid values for sslmode are:
#
# * disable - No SSL
# * require - Always SSL (skip verification)
# * verify-ca - Always SSL (verify that the certificate presented by the server was signed by a trusted CA)
# * verify-full - Always SSL (verify that the certification presented by the server was signed by a trusted CA and the server host name matches the one in the certificate)
dsn="postgres://loraserver_as:xxxxxxx@localhost/loraserver_as?sslmode=disable"
# Automatically apply database migrations.
#
# It is possible to apply the database-migrations by hand
# (see https://github.com/brocaar/lora-app-server/tree/master/migrations)
# or let LoRa App Server migrate to the latest state automatically, by using
# this setting. Make sure that you always make a backup when upgrading Lora
# App Server and / or applying migrations.
automigrate=true
# Redis settings
#
# Please note that Redis 2.6.0+ is required.
[redis]
# Redis url (e.g. redis://user:password@hostname/0)
#
# For more information about the Redis URL format, see:
# https://www.iana.org/assignments/uri-schemes/prov/redis
url="redis://localhost:6379"
# Max idle connections in the pool.
max_idle=10
# Idle timeout.
#
# Close connections after remaining idle for this duration. If the value
# is zero, then idle connections are not closed. You should set
# the timeout to a value less than the server's timeout.
idle_timeout="5m0s"
# Application-server settings.
[application_server]
# Application-server identifier.
#
# Random UUID defining the id of the application-server installation (used by
# LoRa Server as routing-profile id).
# For now it is recommended to not change this id.
id="6d5db27e-4ce2-4b2b-b5d7-91f069397978"
# Integration configures the data integration.
#
# This is the data integration which is available for all applications,
# besides the extra integrations that can be added on a per-application
# basis.
[application_server.integration]
# The integration backend.
#
# This defines the backend to use for the data integration. Use the section
# name of one of the following integration backend.
# E.g. "mqtt" or "gcp_pub_sub".
backend="mqtt"
# MQTT integration backend.
[application_server.integration.mqtt]
# MQTT topic templates for the different MQTT topics.
#
# The meaning of these topics are documented at:
# https://www.loraserver.io/lora-app-server/integrate/data/
#
# The following substitutions can be used:
# * "{{ .ApplicationID }}" for the application id.
# * "{{ .DevEUI }}" for the DevEUI of the device.
#
# Note: the downlink_topic_template must contain both the application id and
# DevEUI substitution!
uplink_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/rx"
downlink_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/tx"
join_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/join"
ack_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/ack"
error_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/error"
status_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/status"
location_topic_template="application/{{ .ApplicationID }}/device/{{ .DevEUI }}/location"
# Retained messages configuration.
#
# The MQTT broker will store the last publised message, when retained message is set
# to true. When a client subscribes to a topic with retained message set to true, it will
# always receive the last published message.
uplink_retained_message=false
join_retained_message=false
ack_retained_message=false
error_retained_message=false
status_retained_message=false
location_retained_message=false
# MQTT server (e.g. scheme://host:port where scheme is tcp, ssl or ws)
server="tcp://localhost:1883"
# Connect with the given username (optional)
username=""
# Connect with the given password (optional)
password=""
# Quality of service level
#
# 0: at most once
# 1: at least once
# 2: exactly once
#
# Note: an increase of this value will decrease the performance.
# For more information: https://www.hivemq.com/blog/mqtt-essentials-part-6-mqtt-quality-of-service-levels
qos=0
# Clean session
#
# Set the "clean session" flag in the connect message when this client
# connects to an MQTT broker. By setting this flag you are indicating
# that no messages saved by the broker for this client should be delivered.
clean_session=true
# Client ID
#
# Set the client id to be used by this client when connecting to the MQTT
# broker. A client id must be no longer than 23 characters. When left blank,
# a random id will be generated. This requires clean_session=true.
client_id=""
# CA certificate file (optional)
#
# Use this when setting up a secure connection (when server uses ssl://...)
# but the certificate used by the server is not trusted by any CA certificate
# on the server (e.g. when self generated).
ca_cert=""
# TLS certificate file (optional)
tls_cert=""
# TLS key file (optional)
tls_key=""
# Google Cloud Pub/Sub backend.
[application_server.integration.gcp_pub_sub]
# Path to the IAM service-account credentials file.
#
# Note: this service-account must have the following Pub/Sub roles:
# * Pub/Sub Editor
credentials_file=""
# Google Cloud project id.
project_id=""
# Pub/Sub topic name.
topic_name=""
# Settings for the "internal api"
#
# This is the API used by LoRa Server to communicate with LoRa App Server
# and should not be exposed to the end-user.
[application_server.api]
# ip:port to bind the api server
bind="0.0.0.0:8001"
# ca certificate used by the api server (optional)
ca_cert=""
# tls certificate used by the api server (optional)
tls_cert=""
# tls key used by the api server (optional)
tls_key=""
# Public ip:port of the application-server API.
#
# This is used by LoRa Server to connect to LoRa App Server. When running
# LoRa App Server on a different host than LoRa Server, make sure to set
# this to the host:ip on which LoRa Server can reach LoRa App Server.
# The port must be equal to the port configured by the 'bind' flag
# above.
public_host="localhost:8001"
# Settings for the "external api"
#
# This is the API and web-interface exposed to the end-user.
[application_server.external_api]
# ip:port to bind the (user facing) http server to (web-interface and REST / gRPC api)
bind="0.0.0.0:8080"
# http server TLS certificate (optional)
tls_cert=""
# http server TLS key (optional)
tls_key=""
# JWT secret used for api authentication / authorization
# You could generate this by executing 'openssl rand -base64 32' for example
jwt_secret="verysecret"
# when set, existing users can't be re-assigned (to avoid exposure of all users to an organization admin)"
disable_assign_existing_users=false
# Join-server configuration.
#
# LoRa App Server implements a (subset) of the join-api specified by the
# LoRaWAN Backend Interfaces specification. This API is used by LoRa Server
# to handle join-requests.
[join_server]
# ip:port to bind the join-server api interface to
bind="0.0.0.0:8003"
# CA certificate (optional).
#
# When set, the server requires a client-certificate and will validate this
# certificate on incoming requests.
ca_cert=""
# TLS server-certificate (optional).
#
# Set this to enable TLS.
tls_cert=""
# TLS server-certificate key (optional).
#
# Set this to enable TLS.
tls_key=""
# Key Encryption Key (KEK) configuration.
#
# The KEK meganism is used to encrypt the session-keys sent from the
# join-server to the network-server.
#
# The LoRa App Server join-server will use the NetID of the requesting
# network-server as the KEK label. When no such label exists in the set,
# the session-keys will be sent unencrypted (which can be fine for
# private networks).
#
# Please refer to the LoRaWAN Backend Interface specification
# 'Key Transport Security' section for more information.
[join_server.kek]
# Application-server KEK label.
#
# This defines the KEK label used to encrypt the AppSKey (note that the
# AppSKey is signaled to the NS and on the first received uplink from the
# NS to the AS).
#
# When left blank, the AppSKey will be sent unencrypted (which can be fine
# for private networks).
as_kek_label=""
# KEK set.
#
# Example (the [[join_server.kek.set]] can be repeated):
# [[join_server.kek.set]]
# # KEK label.
# label="000000"
# # Key Encryption Key.
# kek="01020304050607080102030405060708"you don’t set tls certificates to web interface, did you try to access to web via http://yours-ip:8080 ?
Ok, so I have to buy SSL certificate? and set up in the lora-app-server.toml file?
Yes, I tried running this in web browser: http://my-ip:8080 but did not show anything : it says could not open the page because server stopped responding
can you give me yours public IP of app server?
If tls_cert and tls_key are not set for the external api, then lora-app-server will work over plain http, so you don’t really need a certificate. Also, for local development self signed certificates are perfectly fine, and for public access there’s always Let’s Encrypt to get free certificates.
I haven’t used Digital Ocean, but I found this: https://bobcares.com/blog/digitalocean-open-port-8080/. So it seems that ports other than 80 are not open by default and that’s likely your issue.
Yes, opening the port 8080 on my server solved the issue!! Thank you so much @iegomez !!
Next, what are the login credentials that I can use? or where do I define the admin / superusers for LoraServer login screen?
Thanks
So sorry! The default is admin/admin, I remember now 
Works good!!
Thank you so much all of you for your help!